If I’m honest, this touch bar that new Macbook Pro brings keeps me cold. As system administrator I’m forced to use ESC a lot. This “virtual” escape button on touch bar is annoying as hell. But there is way to make escape button physical again. Sierra brought simple solution to assign escape to caps lock button. Not very good solution in my opinion. I have international keyboard and paragraph/section (§) key is unused – I don’t recall that I ever used section key. So I assigned escape function to section key which is also near to position where escape button used to be, so that makes it even more great.
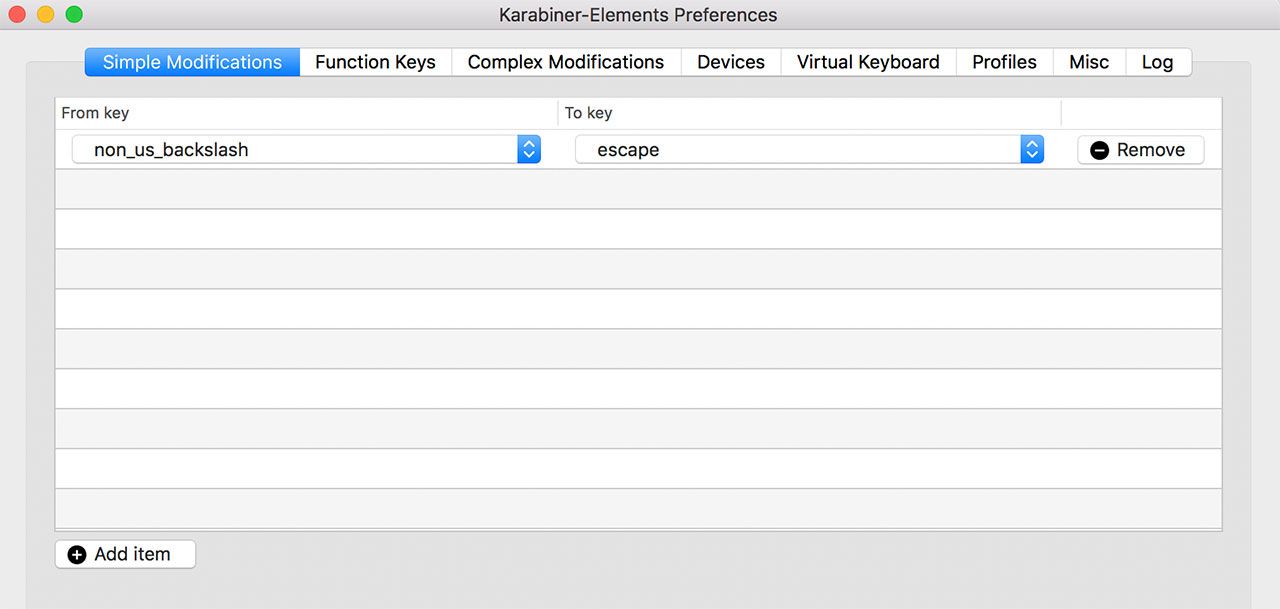
First I installed this Karabiner-Elements. Then you must create simple rule. I was confused when assigning “From key” because section key wasnt there. It turns out that you have to select non_us_backslash option and then assign “To key” escape.
It should look like this:
I hope that this helps anyone 🙂
Recent Comments