Nginx Proxy Manager is a great tool for managing proxy vhosts. Specially useful when dealing with Docker containers. By default, you can access administration from everywhere through default port 81. Here is how you can simply lock it with password or limit it so that is accessible from specified IPs.
First login into admin panel and create Access List which will contain access rules:
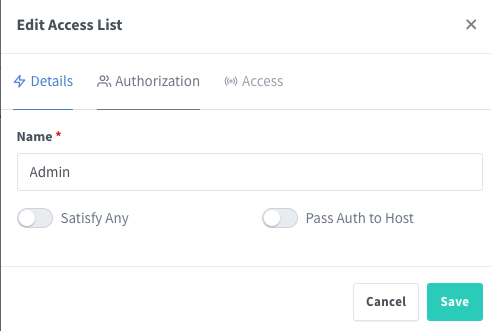
You can limit to be accessible from IPS: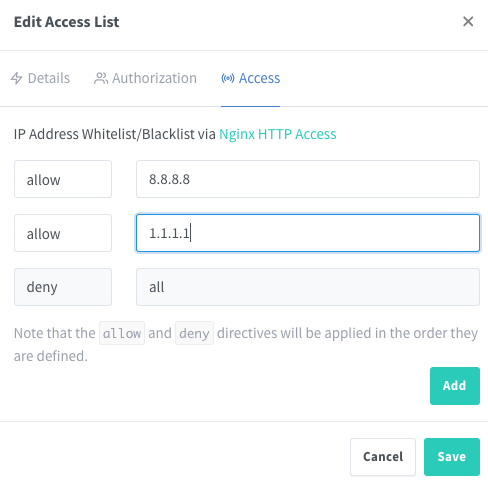
or with password: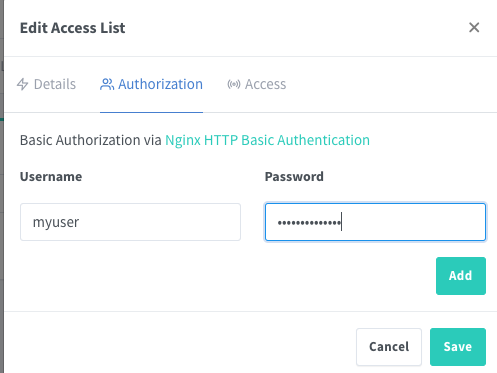
Then, create a new Proxy Host that will have backend set to nginx proxy manager administration. In my case, “proxy-manager” is the host of my nginx proxy manager container. Don’t forget to set Access List to the one that we created in the previous step.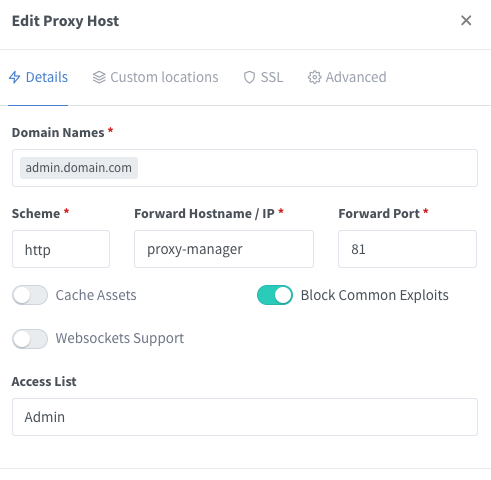
Then change value in your docker-compose file so that port 81 will be on localhost only:
version: '4.3' services: proxy-manager: image: 'jc21/nginx-proxy-manager:latest' container_name: proxy-manager restart: always ports: - "80:80" # Public HTTP Port - "443:443" # Public HTTPS Port - "127.0.0.1:81:81" # Admin Web Port
Administration is now reachable through subdomain https://admin.domain.com/ and only from IPs that we set in above step – or with password. It is advisable that you make some random URL like https://siudhfoisdiishjw0ion094ioejvn.domain.com when creating administration access.
Recent Comments